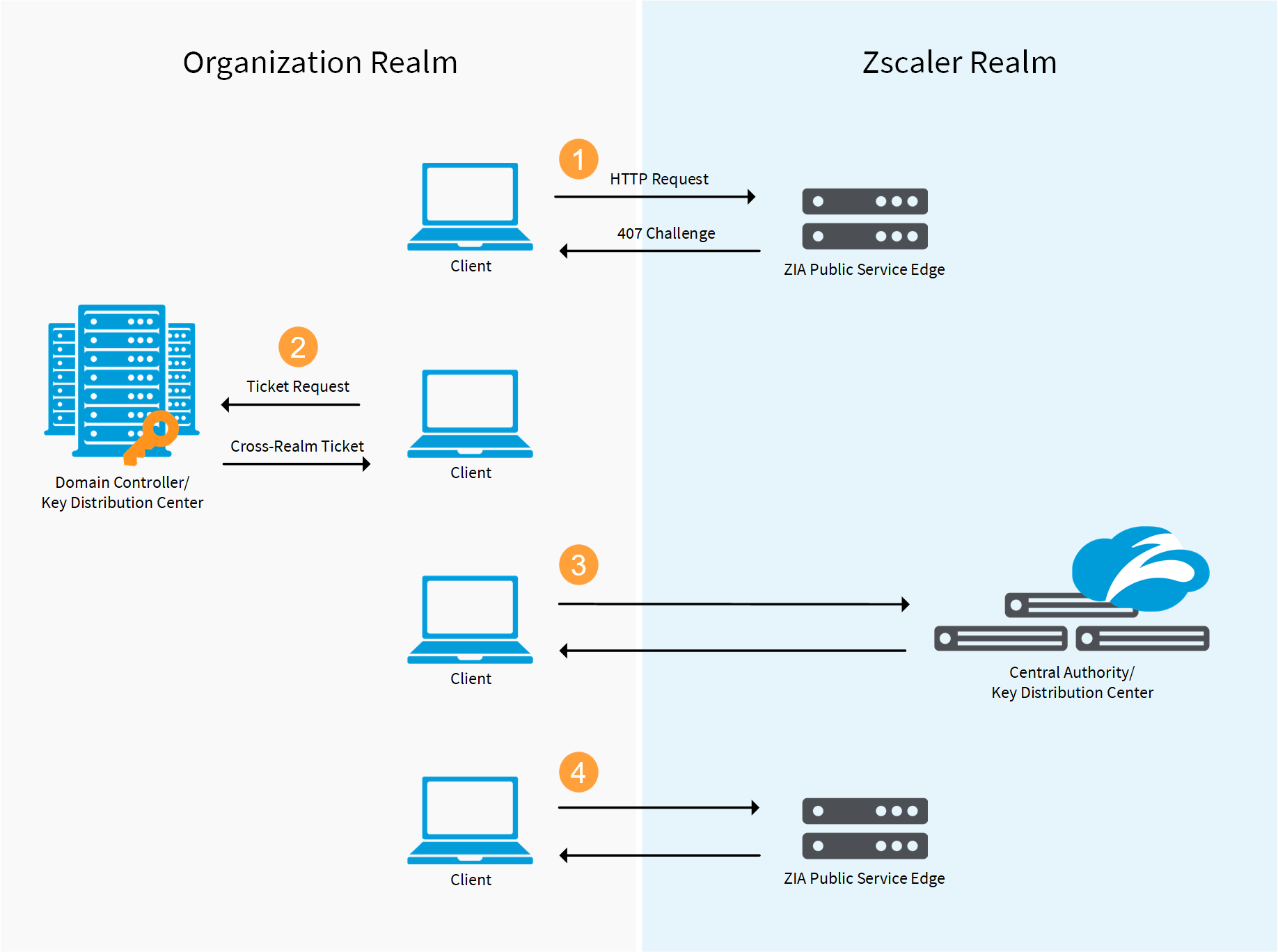
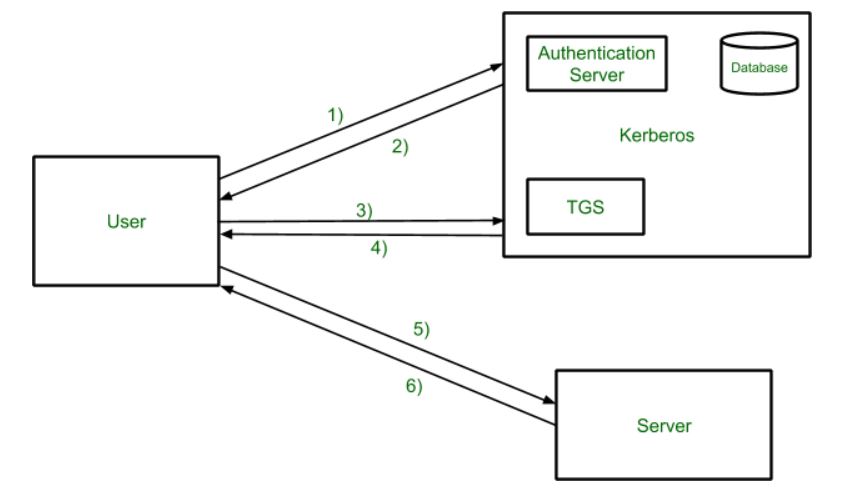
The code will print Authentication Scheme. This property defaults to 10.

Configure Kerberos Server And Client Knoldus Blogs
Nificlusternodeprotocolport - Set this to an open port that is higher than 1024 anything lower requires root.

Kerberos authentication protocol port. However once we name the TCPIP model it had been designed and developed by Department of Defense DoD in. 0x40810010 Result Code. PostgreSQL supports GSSAPI with Kerberos authentication according to RFC 1964.
Typical applications include remote command-line login and remote command execution but any network service can be secured with SSH. Kerberos is a network authentication protocol that uses symmetric key cryptography and requires authorization from a trusted third party to authenticate client-server applications. In the modern world Kerberos is often used as a third-party.
KERBEROS to the console if successful. Its contrary to authentication methods that rely on NTLM. Project Athena was a joint initiative of MIT Digital Equipment Corporation and IBM to build a distributed computing environment for.
The Secure Shell Protocol SSH is a cryptographic network protocol for operating network services securely over an unsecured network. To understand the conceptual framework see Kerberos authentication. Creating user identity which will be used for active directory authentication.
Kerberos is a network authentication protocol. The authentication itself is secure but the data sent over the database connection will be sent unencrypted unless SSL is used. A thread pool is used for replicating requests to all nodes and the thread pool will never have fewer than this number of.
A Kerberos authentication ticket TGT was requested. Run the following code on a Windows machine with working Kerberos authentication to verify if the aforementioned is true. This guide assumes a working Kerberos setup already exists.
The protocol was initially developed at the Massachusetts Institute of Technology MIT as part of a larger project called Project Athena. Well-known port numbers are port numbers for Transmission Control Protocol TCP or User Datagram Protocol UDP that have been assigned to specific TCPIP applications or services by the Internet Assigned Numbers Authority IANA. NTLM is the easiest authentication protocol to use and is more secure than Basic authentication.
In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication. By default NTLM is session-based. Ports used Kerberos is primarily a UDP protocol although it falls back to TCP for large Kerberos tickets.
3 Enabling windows authentication doesnt mean Kerberos protocol will be used. GSSAPI is an industry-standard protocol for secure authentication defined in RFC 2743. It internet protocol suite had been designed to explain the functions of the communication system by dividing the communication procedure into smaller and less complicated parts.
The following example shows host vars configured for Kerberos authentication. As of Ansible version 23 the Kerberos ticket will be. It means that the client must send the Kerberos ticket that can be quite a large blob with each request thats made to the server.
The OSI Model we simply checked out is simply a referencelogical model. This may require special configuration on firewalls to allow the UDP response from the Kerberos server KDC. The Transmission Control Protocol TCP and the User Datagram Protocol UDP only need one port for duplex bidirectional trafficThey usually use port numbers that match the services of the corresponding TCP or UDP implementation if they exist.
The total range of possible port. The UDP packets may not require a special rule if your. For accounts in this group Kerberos protocol verifies authentication at each request.
Nificlusternodeprotocolthreads - The number of threads that should be used to communicate with other nodes in the cluster. It was originally developed by the Massachusetts Institute of Technology MIT to protect the network services provided by the Athena project. Kerberos long-term keys.
Well-known port numbers are assigned within the range 0 through 1023 and are specified in Request for Comments RFC 1060. Negotiate is a. TCPIP Model Layers.
The keys from Kerberos initial TGT requests are typically cached so the authentication requests are not interrupted. 3 Enabling windows authentication doesnt mean Kerberos protocol will be used. Kerberos is an authentication protocol enabling systems and users to prove their identity through a trusted third-party.
GSSAPI provides automatic authentication single sign-on for systems that support it. Kerberos is a request-based authentication protocol in older versions of Windows Server such as Windows Server 2008 SP2 and Windows Server 2008 R2. It might also use NTLM which is also a provider in windows authentication.
Negotiate is a. Using Kerberos authentication from Unix Machines on the same domain. A cached verifier is not created at sign-in.
It might also use NTLM which is also a provider in windows authentication. Das Internet Message Access Protocol IMAP ursprünglich Interactive Mail Access Protocol ist ein Netzwerkprotokoll das ein Netzwerkdateisystem für E-Mails bereitstellt. Kerberos clients need to send UDP and TCP packets on port 88 and receive replies from the Kerberos servers.
It means that the. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication.
IMAP wurde in den 1980er Jahren mit dem Aufkommen von Personal Computern entworfen um bei der Mail-Kommunikation Abhängigkeiten von einzelnen Client-Rechnern aufzulösen. SSH provides a secure channel over an unsecured network by using a clientserver architecture connecting an SSH client. Nebuchadnezzar Supplied Realm Name.
This is a list of TCP and UDP port numbers used by protocols for operation of network applications.

Using External Kerberos Authentication With Amazon Rds For Postgresql Aws Database Blog
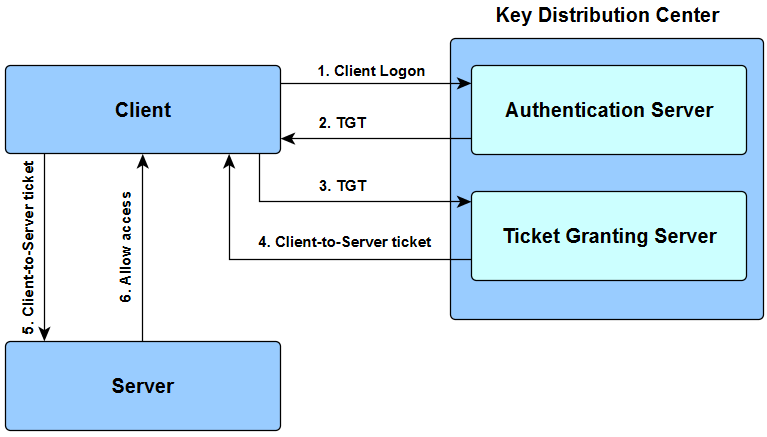
Configuring Kerberos Authentication Protocol Datasunrise Data Db Security

How To Setup Single Sign On Sso For Http Requests Using Spnego Authentication In Liberty
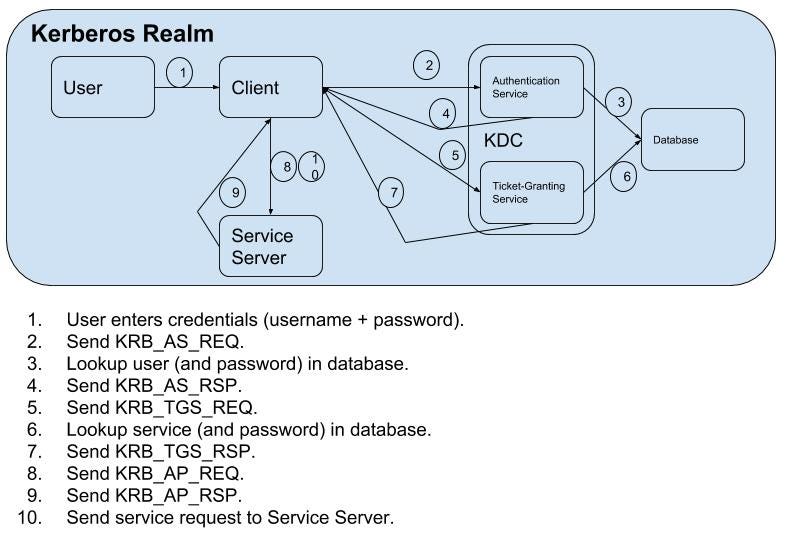
Kerberos And Windows Security Kerberos V5 Protocol By Robert Broeckelmann Medium
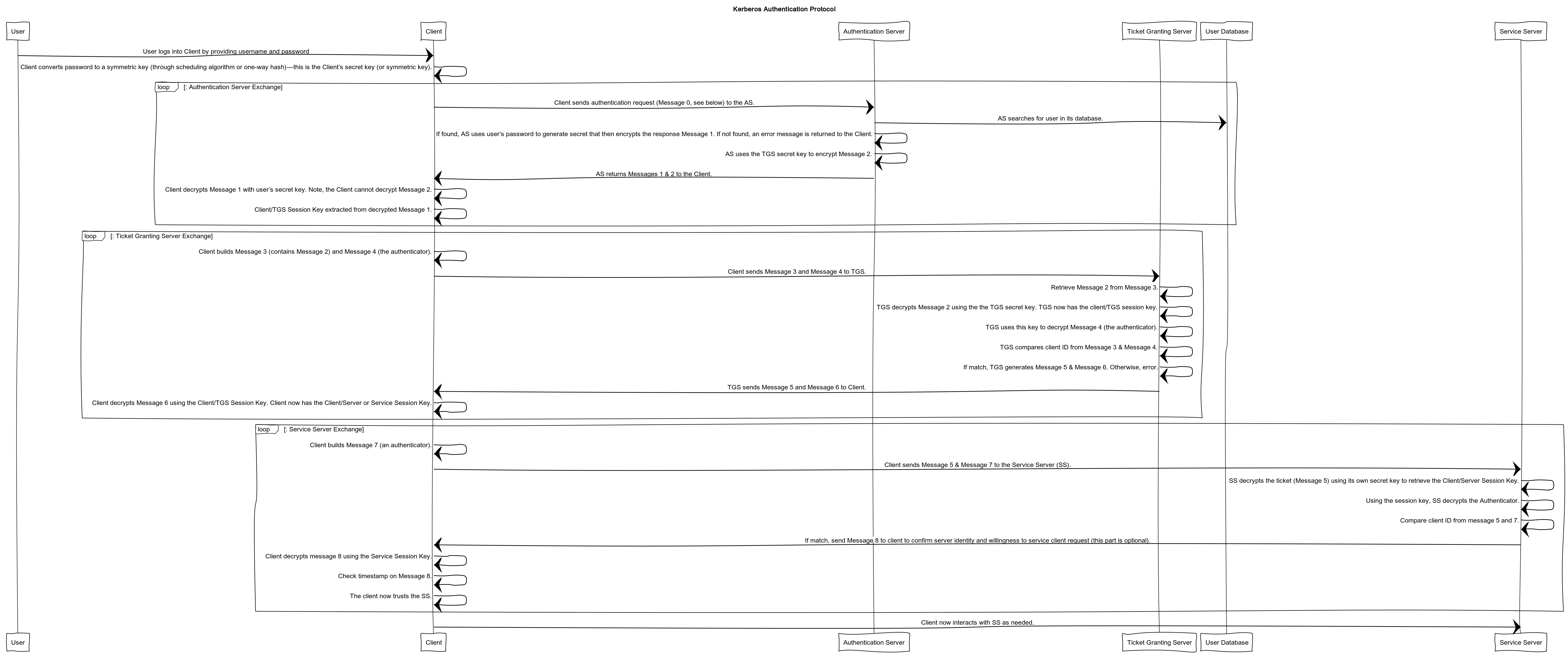
Kerberos And Windows Security Kerberos V5 Protocol By Robert Broeckelmann Medium

Kerberos Authentication An Overview Sciencedirect Topics
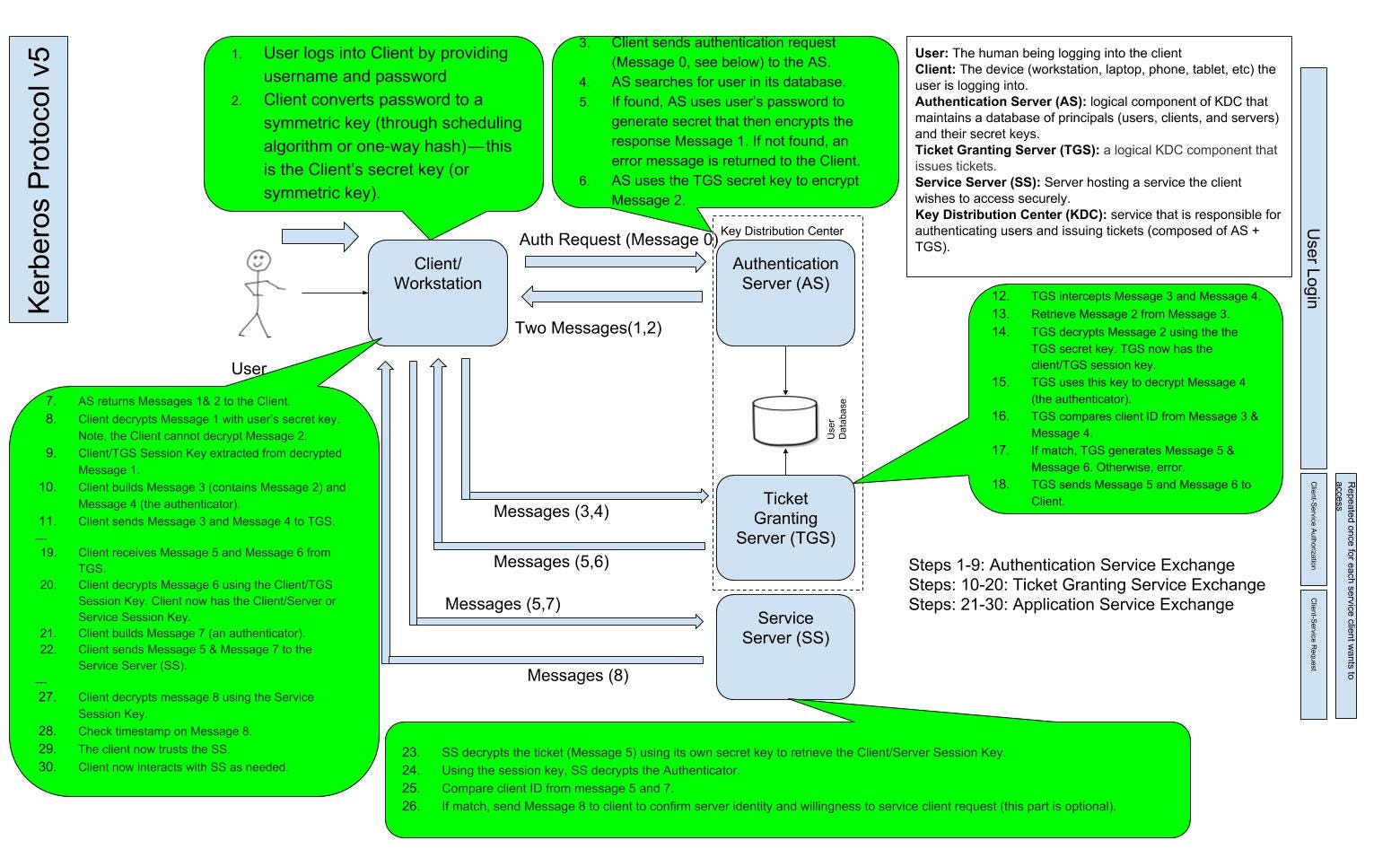
Kerberos And Windows Security Kerberos V5 Protocol By Robert Broeckelmann Medium
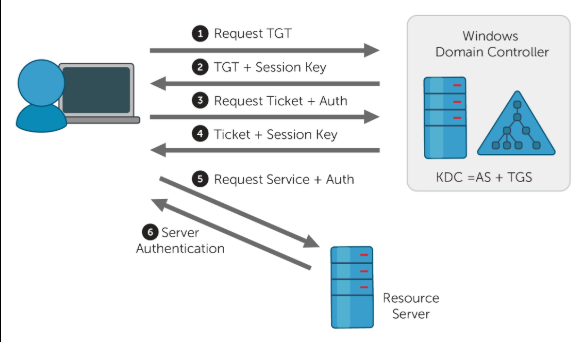
Let S Talk About Kerberos Summary By John D Cyber Jun 2021 Medium

Overview Of Eap Kerberos Authentication In A Roaming Scenario Download Scientific Diagram
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community
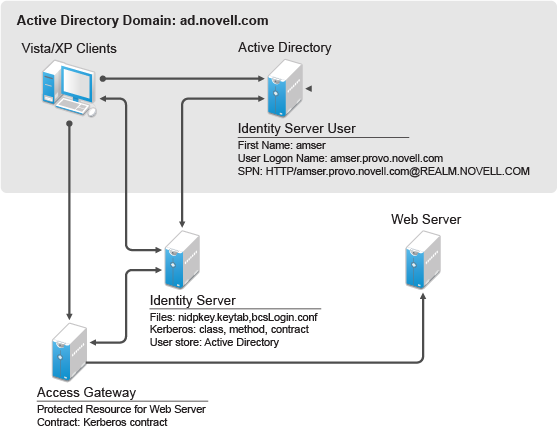
Kerberos Authentication Netiq Access Manager Appliance 4 5 Administration Guide

Kerberos Authentication Protocol With A Smartcard Download Scientific Diagram
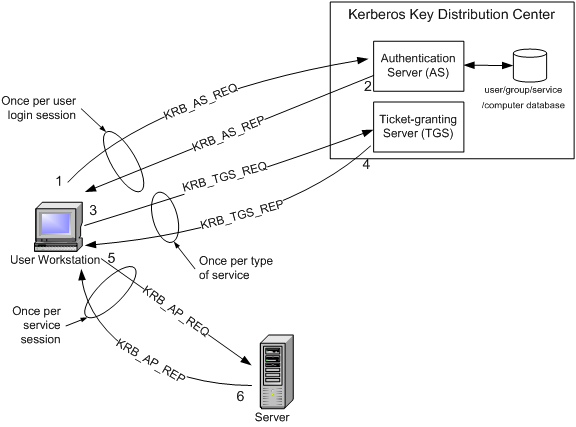
Intel Amt Sdk Implementation And Reference Guide
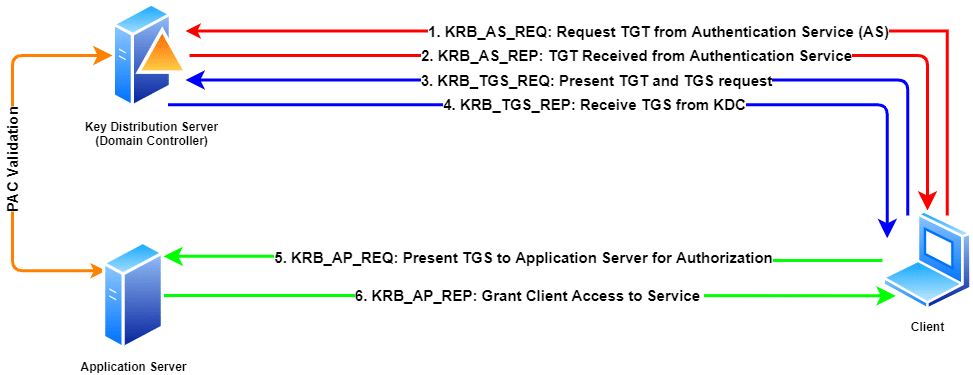
What Is Kerberos Understanding Kerberos What Is It How Does It Work

Kerberos Authentication Axway Open Documentation
Novell Doc Novell Access Manager 3 0 Sp4 Administration Guide Configuring Kerberos For Authentication